Welcome to the Phishing Frenzy, where scammers are fishing for your personal information with the subtlety of a hungry shark! These crafty con artists masquerade as legitimate entities, like your bank or tech support, to reel you in and hook your sensitive data. Let's dive deep into the murky waters of phishing and learn how to spot these pesky predators.
What is Phishing?
Phishing is a type of cybercrime where scammers impersonate trustworthy organizations to trick you into revealing personal information such as usernames, passwords, and credit card details. They use emails, messages, and fake websites that look eerily legitimate (and sometimes extremely horrible) to lure you into their trap.
Let's break down the scammer's toolkit:
- Fake Emails: These emails often come with official logos, fancy signatures, and urgent messages to trick you into thinking they’re legit. But don’t be fooled – they’re as fake as a three-dollar bill.
- Phony Messages: Scammers also use text messages and instant messages that claim you’ve won a prize or that there’s an issue with your account. Spoiler alert: there’s no prize, and your account is just fine.
- Bogus Websites: These websites are designed to look exactly like the ones you trust, from your bank to your favorite online store. The only thing real about them is their intent to steal your information.
Scammers are like digital chameleons, adapting to their environment and blending in seamlessly. But no matter how convincing they seem, their goal is always the same: to fish for your personal data and hook you into a sea of trouble.
The term "phishing" is a playful variation of "fishing," highlighting how scammers bait their victims with tempting lures.
How Phishing Works
Phishing attacks typically follow a simple yet effective formula.
First, the Bait: An email or message appears to be from a reputable source, such as your bank, a popular website, or even a friend. This email often includes recognizable logos and official-sounding language to make it look legitimate.
Next comes the Hook: The message creates a sense of urgency or offers an enticing deal, prompting you to click on a link or download an attachment. This urgency might come in the form of a warning about your account being compromised or an offer that seems too good to pass up.
Then there's the Line: The link directs you to a fake website that looks almost identical to the real one, where you are asked to enter your personal information. This site may be a perfect clone of your bank's login page or a well-known online store, designed to fool even the cautious.
Finally, the Sinker: Once you have entered your information, the scammer has what they need to commit identity theft, fraud, or other malicious activities. Your data is now in their hands, and they can use it to empty your bank account, make unauthorized purchases, or even sell your information on the dark web.
Let's dive deeper into each step to understand the nuances and tactics used by these digital con artists.
- The Bait: Imagine receiving an email that looks like it’s from your bank, complete with their logo and official-looking text. The email says there’s an issue with your account that needs immediate attention.
- The Hook: The email creates a sense of urgency, claiming that if you don’t act quickly, your account will be suspended. This prompts you to click on the provided link to verify your information.
- The Line: The link takes you to a website that looks just like your bank’s login page. It asks you to enter your username and password, along with other sensitive information.
- The Sinker: Once you enter your information, it goes straight to the scammer. They now have access to your account and can commit various malicious activities, such as identity theft or financial fraud.
Always verify the URL of the website before entering any personal information. Scammers often create web addresses that are very similar to legitimate sites, with only slight differences that can be easy to miss. Look for misspellings, extra characters, or unusual domain extensions. If you receive an email or message with a link, it's best to avoid clicking on it directly. Instead, open a new browser window and type the official website address manually. This simple step can save you from falling into a phishing trap.
Understanding this process is crucial to staying vigilant. By familiarizing yourself with these tactics, you can better spot phishing attempts and protect your personal information from falling into the wrong hands. Stay sharp, stay safe, and don’t let those sneaky scammers reel you in!
Common Phishing Scenarios
Bank Scams
Ah, the infamous bank scams, where fraudsters masquerade as your friendly neighborhood banker with all the charm of a used car salesman. In these scams, you receive an email that looks like it's straight from your bank's headquarters. The email subject line alone is enough to give you a mini heart attack: "Urgent: Your Account Has Been Compromised!"
The email body doesn’t waste time with pleasantries. It jumps straight into panic mode, telling you that your account has been flagged for suspicious activity. The language is urgent, the tone is stern, and the message is clear: you must act NOW to save your precious funds from the evil clutches of imaginary hackers.
But hold your horses! Before you click that link faster than you can say “overdraft fee,” take a closer look. This link is the gateway to a fake website, a digital doppelganger of your bank’s official site. It’s designed to trick you into entering your login credentials. The website looks so real you half expect to see your favorite teller’s face pop up in a chat window. The logos are perfect, the layout is identical, but one wrong move, and you’re handing over the keys to your financial kingdom.
Here’s where the scam really gets juicy. Once you enter your login information, it doesn’t go to your bank – it goes straight to the scammer. They now have everything they need to dive into your account and go on a spending spree that would make a shopaholic jealous. They can transfer funds, make purchases, and even lock you out of your own account. It’s like giving a bank robber a guided tour of your vault.
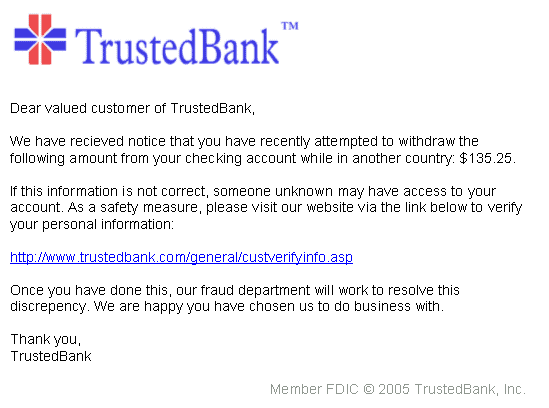
But wait, there’s more! Some particularly nasty scammers might not stop at just your bank account. With access to your email, they can start phishing through your other accounts, looking for more information, more passwords, and more ways to wreak havoc. It’s the gift that keeps on taking.
So, how do you avoid this financial nightmare? Here are some tips to keep your funds safe and your stress levels low:
Tip: Banks will never ask for your login details via email. If you receive such a request, it’s time to hit delete faster than a bad stock tip.
- Always check the sender’s email address. Scammers often use addresses that look similar to your bank’s but with slight variations.
- Never click on links in unsolicited emails. Instead, navigate to your bank’s website directly through your browser.
- Look for generic greetings like “Dear Customer” instead of your actual name. Banks know who you are and will address you personally.
- Watch out for spelling and grammar errors. Legitimate bank communications are usually well-written and professional.
- Enable two-factor authentication on your bank account for an extra layer of security.
Remember, when it comes to bank scams, staying calm and skeptical is your best defense. Don’t let these digital bandits rob you of your hard-earned money. Stay alert, stay safe, and keep those scam emails where they belong – in the trash!
Tech Support Scams
Tech support scams are a sneaky breed of fraud where scammers pose as representatives from well-known tech companies like Microsoft or Apple. You might be peacefully browsing the web when, suddenly, a pop-up message claims that a virus has been detected on your system. The message looks urgent and official, urging you to call a provided phone number for immediate assistance to prevent further damage.
Feeling a mix of panic and urgency, you dial the number. A "tech support" agent answers, sounding professional and reassuring, promising to fix the problem. They instruct you to grant them remote access to your computer, explaining that it's necessary to diagnose and resolve the issue. Trusting their seemingly genuine concern, you comply.
Here's where things take a turn for the worse. Once the scammer has remote access, they can browse through your files, steal personal information, and even install malicious software. Some might hold your computer hostage, demanding a ransom for its release. Instead of solving a problem, they’ve just created a digital nightmare.
To protect yourself from falling victim to these cunning schemes, keep the following tips in mind:
- Ignore unsolicited messages. Legitimate tech companies will not contact you out of the blue about a virus on your computer. If you receive an unexpected message claiming to be from tech support, treat it with suspicion. Real companies don't send random alerts or pop-ups demanding immediate action.
- Verify the source. If you receive a tech support call or message, hang up and contact the company directly using a phone number from their official website. Avoid using contact information provided in the suspicious message. Instead, go to the company's official site and find their support number or email to verify if the contact was genuine.
- Don’t panic. Scammers thrive on creating a sense of urgency. Take a moment to breathe and think before taking any action. Remember, real tech support would never rush you into making hasty decisions. If something feels off, it's better to be safe and double-check before proceeding.
- Keep your software up to date. Regular updates and antivirus software can help protect your computer from actual threats. Ensure that your operating system, applications, and security software are always updated to the latest versions. This practice helps shield your system from vulnerabilities and keeps those pesky scammers at bay.
Real tech support won’t contact you through random pop-ups or unsolicited emails. They are accessible through official channels and legitimate support pages. Don’t let these tech impostors trick you into compromising your computer or your peace of mind. Stay informed, stay cautious, and let these tech support scams fall into the recycle bin of failed attempts.
Warning: Never grant remote access to your computer unless you are absolutely sure of the source. Legitimate companies will never ask for this through unsolicited messages.
Lottery Scams
Lottery scams are the ultimate bait-and-switch, tricking you into believing that you've hit the jackpot in a lottery or sweepstakes you never even entered. It starts with an email that makes your day brighter than a disco ball. The message is filled with congratulations and exclamation points, claiming you’ve won a significant prize, be it cash, a luxury car, or an exotic vacation. Your initial reaction might be to jump for joy and mentally spend that money, but hold your horses!
The email instructs you to click on a link to claim your prize. This link is your golden ticket – or so it seems. Once you click, it leads you to a fake website designed to look as glitzy and official as a real lottery site. This site is the digital equivalent of a con artist in a tuxedo. It asks you to provide personal information, like your name, address, and bank details, and sometimes it even demands a small processing fee to release your prize.
But here’s the kicker – there’s no prize. The only thing you’re winning is a one-way ticket to Scamville. The scammers use the information you provide for identity theft, creating a mess that makes cleaning up after a wild party look easy. And that processing fee you paid? It goes straight into the scammers' pockets, funding their next deceitful venture.
Let’s have a look at the anatomy of these scams and how to outsmart these tricksters:
- Too good to be true. If you didn’t buy a ticket, you can’t win the lottery. Any message claiming otherwise is a scam. Delete it and move on.
- Suspicious links. Always verify the source of the link before clicking. Hover over it to see where it leads. If it doesn’t match the official site, don’t click.
- Request for personal information. Legitimate lotteries don’t ask for sensitive information via email. If they’re asking for your bank details or Social Security number, it’s a scam.
- Processing fees. A true prize doesn’t come with a catch. If you’re asked to pay a fee to claim your winnings, it’s a scam.
So, next time you receive an email claiming you’ve won big, remember to keep your wits about you. Legitimate lotteries don’t operate like surprise parties. Always verify the source, and when in doubt, delete the email. Stay savvy, stay safe, and keep your hard-earned money out of the hands of these scam artists.
Social Media Scams
Social media scams are like the digital version of being catfished by your own friends. Picture this: you’re scrolling through Facebook or Instagram, minding your own business, when suddenly, you receive a message from a "friend." This message is brimming with excitement, claiming they’ve found an interesting article or a hilarious video that you just have to see. Curiosity piqued, you click on the link, eager to see what all the fuss is about.
But hold your horses! Instead of being taken to the promised content, you’re directed to a login page for the social media platform. The page looks legit, right down to the last pixel, but it’s as fake as a three-dollar bill. It prompts you to enter your username and password, and in a moment of distraction, you do.
Congratulations, you’ve just handed over your login credentials to a scammer. These cyber tricksters now have the keys to your social media kingdom. They quickly log into your account, change your password to lock you out, and start sending similar messages to all your contacts. It’s like a digital chain letter, but with way more headaches and potential for damage.
Let’s break down how to spot these scams and protect yourself from becoming a pawn in their game:
- If you receive a message out of the blue from a friend with a link, be cautious. It’s always good to ask them directly if they really sent it.
- Before entering your login details, check the URL of the page. If it looks suspicious or doesn’t match the official domain, do not proceed.
- Enable two-factor authentication on your social media accounts. This adds an extra layer of security and makes it harder for scammers to access your account.
- Messages that push you to click a link immediately should raise a red flag. Scammers often create a sense of urgency to cloud your judgment.
The more people know about these scams, the harder it becomes for scammers to succeed. Share this knowledge and help your friends stay safe too.
Remember, in the world of social media, not everything is as it seems. A little skepticism goes a long way in keeping your online presence secure. Don’t let scammers turn your social media life into their playground. Stay vigilant, stay informed, and keep those scam messages where they belong – in the trash!
How to Spot a PhishingAttempt
To stay safe, be vigilant and look out for the common signs of phishing. Scammers are crafty, but with a keen eye and a skeptical mind, you can spot their traps from a mile away. Here are some tips to help you identify a phishing attempt and avoid becoming the catch of the day:
Scammers often use addresses that look similar to your bank’s but with slight variations. Always inspect the sender’s email address carefully for any inconsistencies or misspellings.
Never click on links in unsolicited emails. Instead, navigate to your bank’s website directly through your browser to ensure you’re visiting the legitimate site.
Look for generic greetings like Dear Customer instead of your actual name. Banks know who you are and will address you personally in their communications.
Legitimate bank communications are usually well-written and professional. Watch out for spelling and grammar errors, which can be a sign of a scam email.
Enable two-factor authentication on your bank account for an extra layer of security. This adds an additional step for verifying your identity, making it harder for scammers to gain access.
Let’s delve a bit deeper into these points:
Check the sender's email address. Scammers often create email addresses that look strikingly similar to legitimate ones. For instance, instead of customer.service@bank.com, you might see customer.service@b4nk.com. That subtle change can easily go unnoticed if you're not paying close attention. Always double-check the email address for any inconsistencies.
Generic greetings. Emails from reputable companies usually address you by your name. If you get an email starting with "Dear Customer", "Valued User", or something equally vague, it's a red flag. Scammers use generic greetings because they send these emails in bulk, hoping to catch someone off guard.
Urgency and threats. One of the scammers' favorite tactics is to create a false sense of urgency. They want you to panic and act without thinking. Emails that threaten to close your account or warn of suspicious activity requiring immediate action are designed to rush you into making a mistake.
Hover over links. A link might say "Click here to verify your account", but when you hover over it, the URL reveals something completely different, like http://scammywebsite.com. This mismatch is a clear sign of a phishing attempt. Always hover to check the real destination before clicking any link.
Spelling and grammar errors. Legitimate companies usually have dedicated teams to ensure their communications are polished and professional. If an email looks like it was written by someone who failed grammar school, it’s a strong indicator that it’s a scam. Typos, weird phrasing, and poor grammar are your cues to delete the email immediately.
By staying alert and scrutinizing these details, you can dodge phishing attempts like a pro. Remember, a cautious approach can save you from a lot of trouble. Keep these tips in mind and you’ll be well-equipped to keep those scammers at bay.
What to Do if You Suspect Phishing
If you suspect an email might be a phishing attempt, taking the right steps can save you from potential trouble. Here’s a detailed guide on what to do:
Avoid Clicking on Links or Downloading Attachments
The first rule of thumb is to avoid clicking on any links or downloading attachments from suspicious emails. These links and files could contain malware or direct you to a phishing site designed to steal your personal information. If an email seems even slightly off, it’s better to err on the side of caution and not engage with any of its content.
Verify the Source
If you're unsure about the legitimacy of an email, take the time to verify the source. Do not use any contact information provided in the suspicious email. Instead, go directly to the official website of the organization and use contact details listed there. For example, if the email claims to be from your bank, use the customer service number on the back of your bank card or visit the bank’s official website to find contact information. By reaching out directly, you can confirm whether the email is genuine or a phishing attempt.
Report the Phishing Attempt
Reporting phishing attempts is crucial in the fight against scammers. Notify your email provider about the suspicious email, as they often have mechanisms to block and filter phishing emails for all users. Additionally, report the email to the organization being impersonated. Many companies have dedicated email addresses or web pages where you can report phishing scams. This helps them take action against the scammers and warn other customers.
Keep Your Software and Security Systems Updated
One of the best defenses against phishing and other cyber threats is to keep your software and security systems up to date. Regular updates help protect your devices from known vulnerabilities that scammers might exploit. Ensure your operating system, web browsers, and antivirus software are all updated to the latest versions. Many updates include patches for security vulnerabilities that could otherwise leave you exposed to phishing attacks.
Educate Yourself and Others
Knowledge is power. Stay informed about the latest phishing tactics and share this information with friends, family, and colleagues. The more people know about these scams, the harder it becomes for scammers to succeed. Consider attending workshops, webinars, or reading articles from trusted sources to keep your knowledge current.
Use Multi-Factor Authentication
Enable multi-factor authentication (MFA) wherever possible. MFA adds an extra layer of security by requiring more than just a password to access your accounts. Even if scammers get hold of your login credentials, they’ll have a much harder time accessing your accounts without that second form of verification.
Final Thoughts
Phishing scams are like the mosquitoes of the internet—annoying, persistent, and potentially harmful. They buzz around, looking for any opportunity to take a bite out of your personal information. But just like dealing with real mosquitoes, a little knowledge and preparation can go a long way in keeping these pests at bay.
Staying informed is your first line of defense. The more you know about how phishing scams work, the better equipped you are to recognize and avoid them. Keep up with the latest scam tactics and educate those around you. Share tips with friends, family, and colleagues so that everyone can stay safe together.
Vigilance is equally important. Always scrutinize emails and messages that ask for personal information or prompt urgent actions. Remember, legitimate organizations won't pressure you to reveal sensitive details through email. When in doubt, verify the source directly and take your time to think before clicking any links or downloading attachments.
On a personal note, think of it as digital self-care. Just as you would apply bug spray before a hike, taking steps to secure your online presence is an essential part of navigating the digital world safely. Use tools like multi-factor authentication and keep your software updated to build a robust defense against these cyber pests.
Remember, you’re not alone in this fight. We’re all part of a community working together to outsmart scammers. By staying sharp and sharing our knowledge, we can turn the tables on these digital tricksters and keep our personal information safe.
Stay savvy, stay secure, and don’t let the scammers bite!
Remember, if it looks too good to be true or makes you panic, take a step back and think before you click. Stay safe and happy surfing!
