In today’s interconnected world, email remains one of the most commonly exploited tools by cybercriminals. Scammers send over 160 billion spam emails daily, accounting for 46% of all email traffic. This staggering volume provides fertile ground for scams like the Pegasus email scam to thrive, as highlighted by recent spam email statistics from EmailToolTester.
The Pegasus email scam capitalizes on the fear surrounding Pegasus spyware, a legitimate surveillance tool, by falsely claiming devices have been infected and demanding ransoms. Understanding these deceptive tactics is essential for protecting your digital life. This article explores how the Pegasus email scam works and offers strategies to keep yourself safe.
Understanding the Pegasus Email Scam
The Pegasus email scam - cybercriminals' latest ploy to ride on the coattails of a very real, very sophisticated spyware tool while peddling their amateur fear-mongering tactics. These scammers aren't exactly the tech wizards they claim to be, but their emails are cunning enough to make even the savviest among us pause.
How the Scam Works
Here’s the gist: You receive an email claiming your devices have been infected with the notorious Pegasus spyware. The scammer, likely typing away in their pajamas, alleges they’ve stolen sensitive information - maybe even compromising photos or videos - and are threatening to release it unless you cough up a ransom, usually in cryptocurrency. Why Bitcoin? Because nothing says, “Trust me, I’m legit,” like demanding payment in untraceable internet money.
Common Tactics Used by Scammers
- Deceptive Emails:
- These fraudsters know how to sound official - or at least, they think they do. Their emails are often riddled with tech jargon designed to make them seem smarter than they actually are.
- Some might even mimic trusted entities to get you to lower your guard. (Spoiler: They're not that convincing.)
- Malicious Links and Attachments:
- Clicking on their links is like signing up for disaster. These URLs often lead to phishing sites that harvest your login credentials or worse. Attachments? Let’s just say “delete without opening” is your best bet.
- Sextortion Campaigns:
- If the email mentions your webcam or compromising videos, take a deep breath. It's a bluff. These scammers are banking on embarrassment to get you to pay up.
- Exploitation of Fear and Urgency:
- “Pay up within 24 hours, or else!” They crank up the pressure, hoping panic will override your critical thinking. Don’t fall for it. The “or else” is just hot air.
The Truth Behind the Scam
Let’s set the record straight: Pegasus spyware is real, but it’s a far cry from what these scammers are claiming. Pegasus requires advanced, state-sponsored attacks - think zero-click exploits deployed by oppressive governments against journalists and political dissidents. These scammers? They’re not hacking geniuses. They’re just con artists using big, scary words to make you panic.
In reality, their claims are bogus. They don’t have Pegasus spyware, and they definitely didn’t hack your devices. All they’re armed with is an email template and your gullibility - don’t give them the satisfaction.
Who’s the Target?
- Everyone with an inbox: Scammers cast a wide net, targeting anyone who might not know how Pegasus spyware actually works.
- The extra paranoid: If you’re a stickler for cybersecurity, these emails are designed to make you doubt yourself.
In short, the Pegasus email scam is a bad joke wrapped in tech jargon. Recognize the red flags, roll your eyes, and move on. You’ve got better things to do than fund a scammer’s coffee habit.
Digital Footprint Awareness
In the vast expanse of the internet, every click, share, and like contributes to your digital footprint - the trail of data you leave behind. While sharing your latest vacation photos or tweeting about your favorite show seems harmless, these actions can accumulate into a detailed profile that cybercriminals eagerly exploit. Understanding and managing your digital footprint is crucial, especially when scams like the Pegasus email scam lurk in the shadows.
The Anatomy of a Digital Footprint
Your digital footprint comprises two main types:
- Active Digital Footprint: Information you intentionally share online, such as social media posts, blog entries, and public profiles. Think of it as your deliberate online persona.
- Passive Digital Footprint: Data collected without your explicit consent, like browsing history, IP addresses, and location data. It's the unintentional trail you leave while navigating the digital world.
Both footprints can be goldmines for cybercriminals. By piecing together bits of your online behavior, they can craft convincing phishing emails, guess your passwords, or, in the case of the Pegasus scam, concoct elaborate stories to extort money.
Why Should You Care?
A sprawling digital footprint increases your exposure to cybersecurity risks. Scammers can analyze your online activities to execute zero-click attacks, where malware is installed on your device without any interaction from you. The less information you broadcast, the harder it becomes for these digital miscreants to target you.
Steps to Manage Your Digital Footprint
- Conduct a Digital Footprint Scan: Regularly search for your name online to see what information is publicly accessible. Tools like Google Alerts can notify you when new information about you appears online.
- Review Privacy Settings: Tighten the privacy settings on your social media accounts to limit who can see your posts. Cyber.ee offers valuable insights into privacy management.
- Limit Personal Data Sharing: Be cautious about the amount of personal information you share online. The less data available, the less ammunition scammers have. Corma Investigations outlines essential strategies to reduce exposure.
- Use Strong, Unique Passwords: Employ complex passwords and change them regularly. Password managers can help you keep track without resorting to "Password123."
- Enable Two-Factor Authentication (2FA): Add an extra layer of security to your accounts. It’s like having a bouncer for your online presence.
- Be Wary of Public Wi-Fi: Avoid accessing sensitive accounts over public Wi-Fi networks. If necessary, use a Virtual Private Network (VPN) to encrypt your connection.
- Regularly Update Software: Keep your operating system and applications up to date to protect against vulnerabilities. Outdated software is an open invitation to cyber intruders.
By taking these steps, you can shrink your digital footprint, making it more challenging for scammers to exploit your online identity. Remember, in the digital realm, less is often more - especially when it comes to sharing personal information.
Identifying Pegasus Scam Emails
The Pegasus email scam thrives on fear, confusion, and urgency, coercing victims into impulsive decisions. These emails are crafted to look alarming, preying on your insecurities and limited knowledge about spyware. However, most of their claims are smoke and mirrors, and identifying these scams is the key to avoiding their traps.
Common Characteristics of Pegasus Scam Emails
Scammers use predictable patterns in their emails, making them relatively easy to spot if you know what to look for:
- Alarming Subject Lines:
Subject lines are designed to grab your attention immediately. They often include phrases like "Your device is compromised" or "Immediate action required", aiming to create panic and push you into opening the email without hesitation. This tactic exploits your instinct to protect your privacy. - Threatening Language:
The body of these emails often claims that your device has been hacked and sensitive information - such as browsing data, private photos, or even webcam recordings - has been accessed. They allege they've recorded compromising videos, a common sextortion tactic, and threaten to release this "evidence" to your contacts unless you comply. - Cryptocurrency Ransom Demands:
Scammers demand payment in Bitcoin or another cryptocurrency, which is untraceable and provides them anonymity. They usually include a crypto wallet address and specify a deadline, such as 48 hours, to amplify the sense of urgency. - Urgency and Pressure:
Phrases like "You have 24 hours to respond" or "This is your final warning" are used to heighten anxiety. By creating a false sense of urgency, scammers aim to override your logical thinking and force you to act out of fear. - Poor Grammar and Spelling:
Despite claiming to be sophisticated hackers, many scam emails are riddled with typos and awkward grammar. These errors are often overlooked by victims in moments of panic but serve as a clear indicator of fraudulent activity.
Real-Life Example
Here’s an example of a Pegasus scam email:
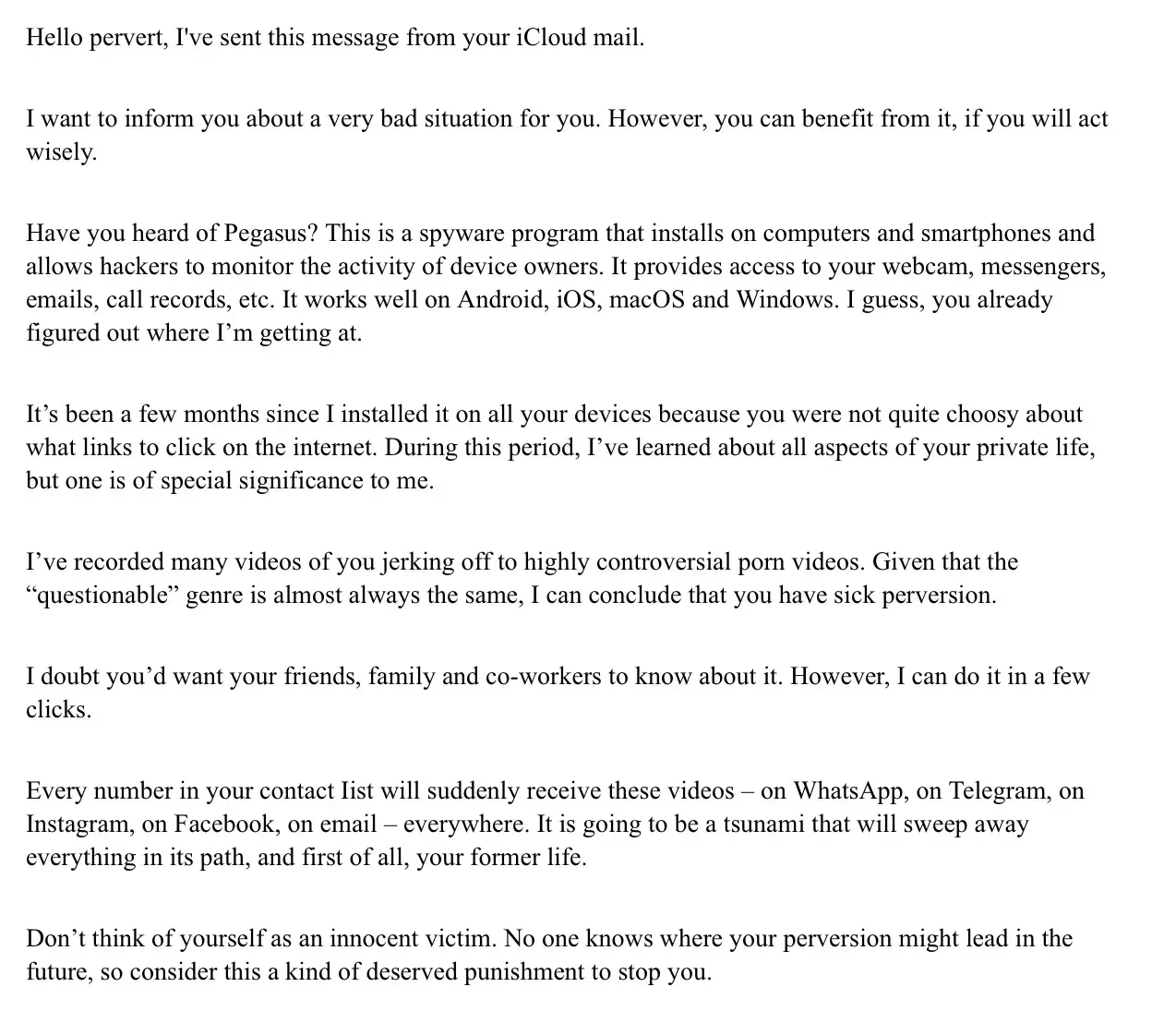
Why These Claims Are False
Pegasus spyware is real, but deploying it requires advanced, resource-intensive methods typically reserved for targeting high-profile individuals like journalists or activists. Scammers behind these emails lack the expertise, resources, or infrastructure to infect random devices at scale. Their claims of hacking and spying are unfounded, relying on your lack of technical knowledge to appear credible.
Immediate Actions if You Receive a Pegasus Scam Email
If you receive an email claiming to be from a Pegasus scammer, follow these steps:
- Do Not Respond: Ignoring the email is your best option. Any response confirms that your email address is active, potentially leading to more scams.
- Avoid Clicking Links or Downloading Attachments: These emails may include phishing links or malware. Treat any attachment or link with extreme caution.
- Report the Email: Use your email provider’s phishing report function. This not only flags the scam for others but also helps improve spam filters.
- Block the Sender: Ensure that future emails from the same sender are automatically filtered out.
- Change Your Passwords: If the email mentions a password you’ve used, change it immediately across all accounts where it was used. Consider using a password manager to generate and store secure passwords.
- Enable Two-Factor Authentication (2FA): Add an extra layer of security to your accounts. Even if someone has your password, they’ll be blocked without access to your 2FA method.
- Run a Security Scan: Use reputable antivirus software to ensure your devices are free from malware or spyware. This step helps reassure you that no actual breach has occurred.
Why Vigilance Matters
Scammers succeed by exploiting fear and urgency. Recognizing the hallmarks of Pegasus scam emails allows you to stay calm and avoid falling victim to their tactics. Remember, their claims are empty threats designed to pressure you into paying a ransom. Armed with knowledge, you can protect your data and deny scammers the satisfaction of success.
Evaluating the Threat Level of Pegasus Scam Emails
Receiving an email claiming your device is infected with Pegasus spyware can be alarming. However, it's essential to assess the credibility of such threats before succumbing to panic.
Have You Really Been Hacked?
In most cases, no, you have not been hacked. The Pegasus email scam is a widespread extortion tactic where cybercriminals send fraudulent emails alleging they've compromised your device using Pegasus spyware. Their goal is to intimidate you into paying a ransom, typically in cryptocurrency. These claims are baseless and designed to exploit your fear.
Understanding Pegasus Spyware
Pegasus is a sophisticated spyware developed by the NSO Group, primarily used by government agencies to monitor high-profile targets like political figures, journalists, and activists. It employs advanced methods, including zero-click attacks, to infiltrate devices without user interaction. Deploying Pegasus requires significant resources and is unlikely to be used against ordinary individuals.
Assessing the Credibility of the Threats
Several factors undermine the credibility of these scam emails:
- Generic Content: Scam emails often use generic salutations and lack personal details, indicating a mass-sent message rather than a targeted attack.
- Lack of Technical Specificity: Legitimate notifications of device compromise would include specific details, such as the nature of the breach, affected data, and steps for remediation. Scam emails typically lack this information.
- Absence of Evidence: Scammers claim to have compromising data or recordings but fail to provide any verifiable proof. This lack of evidence is a strong indicator of deceit.
Recommended Actions
If you receive such an email:
- Do Not Engage: Avoid responding or making any payments. Engaging can encourage further scam attempts.
- Report the Email: Use your email provider's reporting features to mark the message as phishing or spam.
- Maintain Security Hygiene: Ensure your devices have updated security software, use strong, unique passwords, and enable two-factor authentication to protect against genuine threats.
Sources of Data Breach in Pegasus Scam Emails
Have you ever wondered how scammers behind the Pegasus email scam got their hands on your personal information? It’s not cybercriminal sorcery; it’s the result of data breaches, cyberattacks, and the rampant trade of sensitive data on the dark web.
One common way your information might be exposed is through phishing attacks. These scams trick people into revealing login credentials, financial details, or other private information by impersonating legitimate organizations. Phishing remains a major cause of data breaches, with nearly 90% of incidents tied to some form of social engineering. Meanwhile, data breaches targeting large organizations - banks, email providers, or online retailers - also contribute significantly. Hackers infiltrate databases and steal sensitive information, which often ends up for sale on the dark web.
Another factor is the role of data brokers. These companies collect and sell consumer information for marketing purposes. Unfortunately, some of these brokers have inadvertently - or negligently - provided detailed personal datasets to scammers, making it easier for them to craft targeted schemes. Add to this the issue of social engineering, where scammers manipulate victims into sharing sensitive data directly. By exploiting fear or pretending to represent trusted entities, they can extract valuable information without deploying any advanced hacking techniques.
How Scammers Use Stolen Data
Once cybercriminals have access to your information, they use it in various ways:
- Crafting convincing scam emails: With details like your name, email address, or even passwords, scammers create personalized messages designed to look legitimate and manipulate you into compliance.
- Identity theft: Personal information can be used to impersonate you, enabling unauthorized access to your financial accounts or creating new accounts in your name.
- Dark web trade: Stolen data is often sold to other criminals who use it for various fraudulent activities, perpetuating the cycle of cybercrime.
Public Wi-Fi networks are another threat vector. Using an unsecured Wi-Fi connection without adequate protection can expose your data to interception by cybercriminals. This can lead to unauthorized access to your personal information or even compromise your login credentials.
Protecting Your Personal Information
To minimize the risk of your data falling into the wrong hands, consider the following steps:
- Be cautious of unsolicited communications: Avoid clicking on links or downloading attachments from unknown sources, especially if they seem suspicious.
- Use strong, unique passwords: Ensure each account has its own complex password, and update them regularly to prevent breaches from spreading across accounts.
- Enable two-factor authentication (2FA): Add an extra layer of security to your accounts, making unauthorized access significantly more difficult.
- Monitor financial and credit statements: Regularly review for unauthorized transactions or accounts created in your name.
- Stay informed: Educate yourself about the latest cybersecurity threats and strategies to protect your data.
By understanding the various sources of data breaches and the methods scammers use, you can take proactive measures to safeguard your personal information and reduce your risk of becoming a victim of scams like Pegasus.
Wrapping It Up
The Pegasus email scam is just one of many tactics cybercriminals use to exploit fear and misinformation. By claiming access to sensitive data and demanding cryptocurrency ransoms, these scammers hope to trick you into acting impulsively. However, their threats are hollow, relying entirely on your panic rather than any real hacking capabilities.
Staying safe in the digital world means staying informed. Understanding how scams like this operate, recognizing their telltale signs, and knowing how to respond are critical steps in protecting yourself. Whether it’s spotting poorly written emails, ignoring cryptocurrency ransom demands, or taking proactive measures like enabling two-factor authentication, every action you take reinforces your defenses against these threats.
Remember, the best way to beat scammers at their own game is to deny them what they seek - your trust, your attention, and your money. So, keep your digital footprint in check, stay skeptical of unsolicited emails, and never let fear dictate your decisions. Knowledge is your greatest weapon in the fight against cybercrime, and with it, you’ll always be one step ahead of the scammers.

